
Banking and financial sector have always been the prime target for cyber-attacks. This sector holds the most valuable information from accounts and credit card data to sensitive Personally Identified Information. As such, these sectors are always on the forefront, they are more vulnerable to the cyber-attack. The COVID-19 pandemic has boosted the threats, as financial institutions already large exposed, risks has been amplified by sudden shifts to remote working practices and other operational challenges the risk. With this increase in threats, a new generation of cyber criminals is also evolving. These cyber-criminals are no longer satisfied with simply stealing funds and holding companies’ information hostage, instead, aiming to infiltrate and manipulate companies and environments, threatening the credibility and integrity of the institution, leaking sensitive information to the public, or committing fraud at different levels. The financial services sector has always been highly targeted due to the tremendous value of and access to extremely sensitive data and the possibility to quickly make a lot of profit. Cyberattacks can undermine the integrity of a financial organization’s underlying infrastructure as well as the systems that drive its operations.
Recent news about Nepal
In July 2021, 15 banks in Nepal were threatened for hacking the banking system. The group sent an email illustrating that the system has been compromised. The email created lots of panic in the banking industries, but later nothing happened.
Well, again in December, an email has been sent threatening to compromise various systems of the bank. Threats are always better to be analyzed. Not good to be ignored. However, the stress it is creating for the industry and the professional also cannot be ignored.
Threat Actors
Certain threats actors are responsible for the more complex cyber-attack and campaigns. They mostly attack the confidentially, availability and integrity of the organizations. Some of the most active threat actors that targets the finical sectors are
- Lazarus group: Lazarus group have been active from 2009. This group has been linked with the most notorious hacks, including the 2014 attack against the Sony Picture Entertainment, 2016 Bangladesh bank heist, 2017 ransomware. Lazarus has continued to target financial institutions with the goal of carrying out SWIFT heists. s. In recent years, targets included financial institutions in the US, Mexico, Brazil, Chile, Venezuela, Colombia, Uruguay, UK, Denmark, Poland, Turkey, China, Taiwan, and Hong Kong.
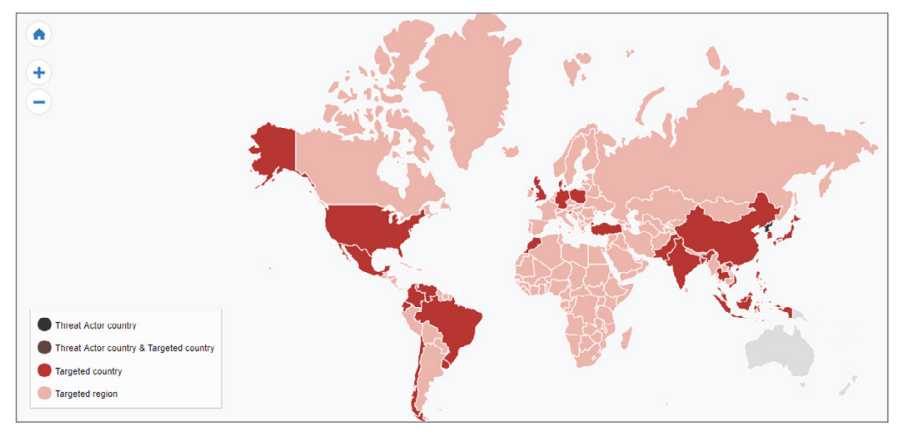
Nations target by Lazarus Group
- Mustang Panda: Mustang Panda is a China-based cyber espionage threat actor that was first observed in 2017 but may have been conducting operations since at least 2014. Mustang Panda has targeted government entities, non-profits, religious, and other non-governmental organizations in the U.S., Germany, Mongolia, Myanmar, Pakistan, and Vietnam, among others.
-
SideWinder: Sidewinder is a suspected Indian threat actor group that has been active since at least 2012. They have been observed targeting government, military, and business entities throughout Asia, primarily focusing on Pakistan, China, Nepal, and Afghanistan.
APT37: APT37 is a North Korean state-sponsored cyber espionage group that has been active since at least 2012. The group has targeted victims primarily in South Korea, but also in Japan, Vietnam, Russia, Nepal, China, India, Romania, Kuwait, and other parts of the Middle East. APT37 has also been linked to the following campaigns between 2016-2018: Operation Daybreak, Operation Erebus, Golden Time, Evil New Year, Are you Happy?, FreeMilk, North Korean Human Rights, and Evil New Year 2018
Initial Infection
The process by which cyber-attack is carried out can be described as the life cycle. The initial reconnaissance is the crucial to determine whether the cyber- attack will be successful or not. Human is the weakest link in the security, and social engineering is the first choice of the Advance Persistence Threat Actor. Threat actors like Lazarus group, Mustang Panda, Sidewinder use the spear phishing techniques. Mustang Panda compromise the target with the help of weaponized PDF and word documents that drops via spear-phishing email with VBScript embedded in the “.lnk”. Lazarus group used the similar method. They study the publicly available information about the target and sent phishing email that either had a malicious Word document attached or a link to one hosted on a remote server.
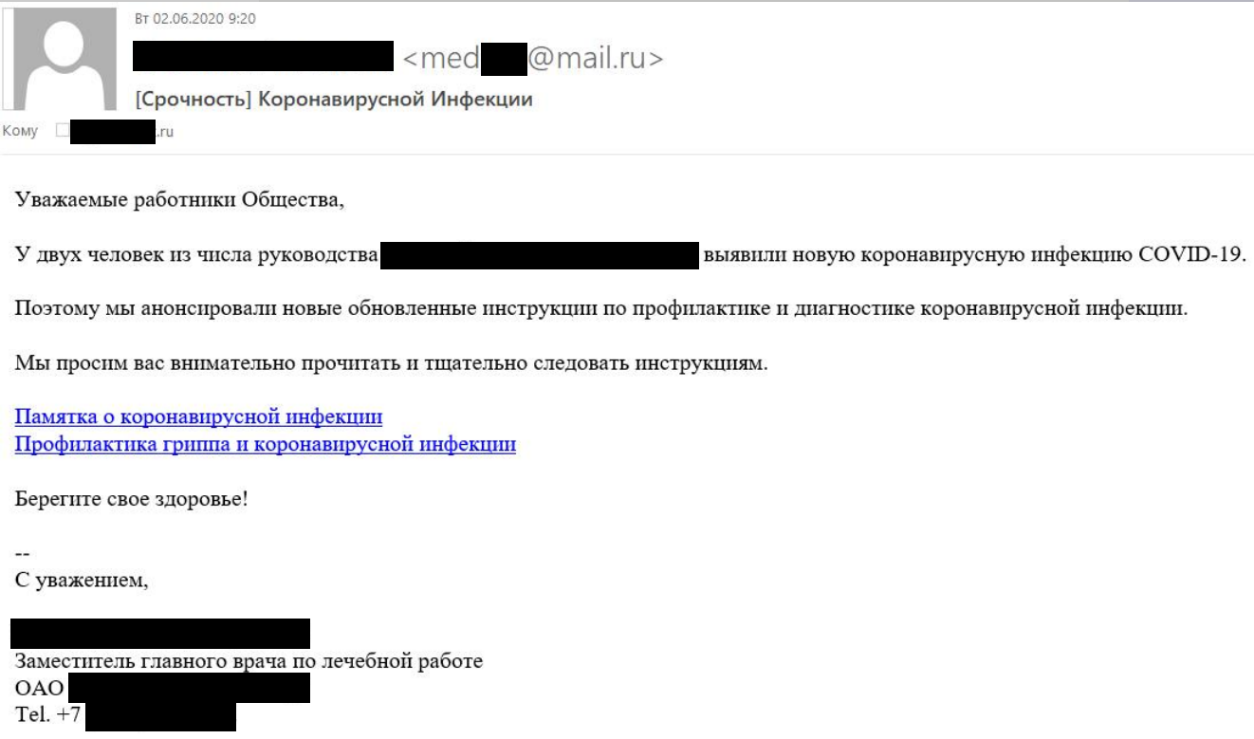
Phishing email sent by lazarus group
Preventive measure
- Multi-Factor Authentication: Organizations can implement multi-factor authentication protocols to prevent attacks. MFA systems function as core elements of identity and access management models.
- Raise fraud awareness: Provide employees with greater levels of education surrounding financial fraud. Corporate accounts can be taken over, employees’ desktops can be accessed remotely, and ransomware represents a very clear and present risk
- Implement Logging and Monitoring: Logging and monitoring are essential to ensuring a business can react quickly and effectively to security incidents. It provides an auditable trail which can be used by your security team to assess the situation and isolate the cause
- Create Disaster Recover: In the event of a disaster be it caused by environmental factors, a security breach or anything which may prevent your business from performing its day-to-day business needs, consider what procedures or redundancy you have in place as an organization to prevent downtime and continue conducting business Plan
- Zero-trust network model: While zero-trust has existed for quite some time by now, not all organizations have adopted it. Layering zero-trust policies into your security architecture can limit liabilities in the event of a network intrusion
- Email Security: Email is the most common attack vectors. Implantation of email security solution such as Email-security gateway, DMARC, SPF prevents the unauthorized access and impersonations attacks.
- Timely update of the software: Multiple vulnerabilities are reported on daily basis by the security researcher all around the world. Patch is released by the vendors. Timely update will apply patches and reduces the risk of cyber-attack.