Background

Humans don’t tend to think of themselves as vulnerable. As they get sick, natural disaster comes in, they lose their near owns, they get old, then they realize that the only thing they can control is themselves. Control mind, heart, and plan for what could come next.
In prior days we had nuclear weapons, terrorism which was a threat to the nation and society, now we have the Internet.
Data Center, cloud, all your photos, your personal information that is in the cloud and data center are vulnerable. Data Center power majority of thing in your life including satellites, bankings. There can be a significant impact if someone breaks into the system and manipulates this information.
The source for Internet service providers (ISPs) has demonstrated that the number of Internet users has an annual incremental increase of 50%. In 2000, there were only 35,000 users. The number had grown 10 times by 2009, which has shown that there is indeed a growing trend for ICT applications and Internet consumption in Nepal. Cyber Criminals adapting to the changes in technology faster than security solutions are being made.
As of mid-May, 90.56 percent of the population in Nepal had access to the internet, according to the management and information report of the Nepal Telecommunications Authority.
Nepal has moved up to the 94th position in the Global Cybersecurity Index 2020 from the 106th slot in the 2018 edition, showing that its commitment to cybersecurity has increased, according to the International Telecommunication Union (ITU). The Himalayan republic scored 44.99 out of 100 points among 182 countries. It was placed 17th among the 18 countries in the Asia-Pacific region, said the ITU.
2015 and 2016 Russia break into the electric grid of Ukraine and shut off power for a few hours. A nation is believed to intervene in the 2016 US election and altered how Americans perceived narratives around politics. This ultimately is believed to have an impact on the national political situation.
These are some significant consequences that change what you going to think about security.
If you think about someone is going to the beach that security, think that you are vulnerable, then that changes what you think about security. We need to secure our critical infrastructure. We need to implement best practices in cyber resilience.
We need Security for our infrastructure beyond
the beach. We must be resilient to the beach.
Cyber Incidents
There have been many incidents around the world with many security incidents. Some of the biggest cyberattacks are:
- The second-largest software vendor in Germany and the seventh-largest in Europe, Software AG has been reportedly hit by a ransomware attack in October 2020.
- French IT service giant Sopra Steria was attacked by ransomware on the evening of 20th October, as confirmed by the company.
- In September 2020, hackers gained access to Telegram messenger and email data of some big names in the cryptocurrency business.
- The Chicago-based leading global legal firm, Seyfarth Shaw LLP became a victim of an “aggressive malware” attack. This attack was later confirmed by the firm as a ransomware attack. The cyber-attack reportedly took place on October 10, 2020, and downed the firm’s email system completely, as per a statement published by the company.
- The world’s largest cruise line operator, Carnival Corporation reported a data breach due to a ransomware attack that took place in August 2020.
Security landscape in Nepal
In 2016, Metropolitan Police Crime Division arrested Bikash Paudel of Balaju in Nagarjun Municipality on the charge of hacking over 200 official websites of government and non-governmental organization. Hacked the websites of National Tuberculosis Centre, Nepal Telecom, Dairy Development Corporation, Office of Cottage and Small Industries, various educational institutions, among others, besides stealing details of the website users.
- Over 58 government websites, including those of Department of Passports and Nepal Law Commission, were hacked in the past one year in 2017
- Good number of e-banking, payment service providers were found vulnerable to clickjacking, Poodle and security flaws.
- 2017 - An online newspaper has become victim of Wanna-cry in Nepal.
- There was a shift banking attack in NIC bank. The overall amount of money stolen from the bank was around Rs 460 million, Rs 400 million has been retrieved.
- August 2019, the hackers were arrested for stealing millions of rupees from the bank accounts of subscribers by forging their ATM cards. NEPS - ATM service provider for many banks was under cyber-attack. Issued information that it is going to replace all its hardware.
· In March 2020, on Saturday night, Foodmandu, an e-commerce firm distributing on-demand food distribution accommodations throughout the Kathmandu region, witnessed a data breach from their system. The hackers have leaked the database consist of more than 50,000 Utilizer denominations, personal detail, latitude, longitude, current address, emails, and phone number.
· In April 2020, Vianet’s Data Breach Exposes More Than 1.7 Lakhs Customers Personal Data
· In July, 15 banks in Nepal were threatened for hacking the banking system. The group sent an email illustrating that the system has been compromised. The email created lots of panic in the banking industries, but later nothing happened.
· In December, an email has been sent threatening to compromise various systems of the bank. Threats are always better to be analyzed. Not good to be ignored. However, the stress it is creating for the industry and the professional also cannot be ignored.
Cyber Security Actors
Certain threats actors are responsible for the more complex cyber-attack and campaigns. They mostly attack the confidentially, availability and integrity of the organizations. Some of the most active threat actors that targets the finical sectors are
· Lazarus group: Lazarus group have been active from 2009. This group has been linked with the most notorious hacks, including the 2014 attack against the Sony Picture Entertainment, 2016 Bangladesh bank heist, 2017 ransomware. Lazarus has continued to target financial institutions with the goal of carrying out SWIFT heists. s. In recent years, targets included financial institutions in the US, Mexico, Brazil, Chile, Venezuela, Colombia, Uruguay, UK, Denmark, Poland, Turkey, China, Taiwan, and Hong Kong.
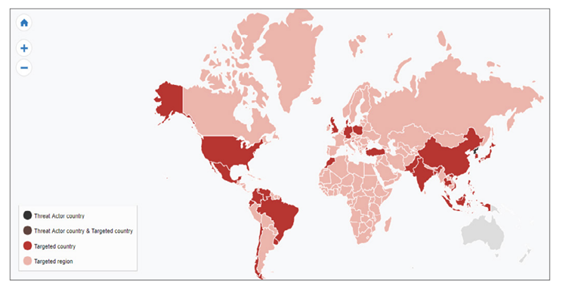
· Mustang Panda: Mustang Panda is a China-based cyber espionage threat actor that was first observed in 2017 but may have been conducting operations since at least 2014. Mustang Panda has targeted government entities, non-profits, religious, and other non-governmental organizations in the U.S., Germany, Mongolia, Myanmar, Pakistan, and Vietnam, among others.
· SideWinder: Sidewinder is a suspected Indian threat actor group that has been active since at least 2012. They have been observed targeting government, military, and business entities throughout Asia, primarily focusing on Pakistan, China, Nepal, and Afghanistan.
· APT37: APT37 is a North Korean state-sponsored cyber espionage group that has been active since at least 2012. The group has targeted victims primarily in South Korea, but also in Japan, Vietnam, Russia, Nepal, China, India, Romania, Kuwait, and other parts of the Middle East. APT37 has also been linked to the following campaigns between 2016-2018: Operation Daybreak, Operation Erebus, Golden Time, Evil New Year, Are you Happy?, FreeMilk, North Korean Human Rights, and Evil New Year 2018. Different Neighboring Countries have published news considering Nepal Cyber Security Situation.
Nepal Under China Shadow for north Korean cyber crimes
October 12, 2020, Japan’s News has claimed - “The concern is the fast-growing and spreading North Korean cyber threat and operations with linkages extending to Nepal in South Asia, as recent reports have brought out.”
"Evil flower in South Asia, lure of beauty, ghost war elephants roaming the Himalayas are the code names for real groups from India with possible intelligence background and state support”
Cyberattacks from groups in India targeted China, Pak & Nepal, claims Chinese media
November 5, 2021, China’s News has claimed – “groups from India with possible intelligence background and state support constantly attacked defence and military units as well as state-owned enterprises in China, Nepal and Pakistan over the past few years”
North-Korean hackers, increasing Chinese intelligence presence in Nepal a fresh cause of worry for India
September 23, 2020, India’s News has claimed – “North Korean nationals operating illegal hacking from the busiest neighbourhood in the capital city of Kathmandu shows Nepal’s homeland security could be in threat”
Shortage of Human Resources
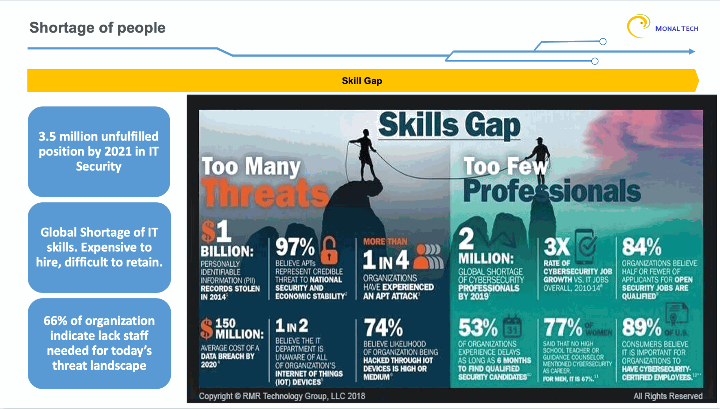
The demand for professionals with cybersecurity skills is continuing to outpace supply, putting many organizations at risk: A 2017 study led by Frost & Sullivan predicted that the global cybersecurity workforce gap will reach 1.8 million by 2022, a 20% increase over the forecast the firm made in 2015. According to ISACA, the “ratio of qualified applicants to open positions leaves much to be desired from the point of view of an enterprise trying to recruit the right security team members.”
Sectors and its situation in Nepal
Nepal’s IT industry is small, but the digitization is growing rapidly. Many people/organizations are still unknown about the different threats and cyber-attacks, so vast amounts of data across the public and private domains are at risk. Due to increments of different cyber-attacks in Nepal, the people and the organizations both should be aware of it and should implement a different strategy to be safe from different cyber-attacks. Different sectors that are affected by cyber treats are:
Financial Sector
Despite banking cyber security standards and healthy cyber security investment levels, financial firms continually see themselves on “most-hacked industries” lists. This undesirable achievement doesn’t mean that security is poor. Rather, threat actors disproportionately target the industry due to the availability of financial and data assets.
Nepal Financial situation
- NRB has regulated guidelines for cyber security controls and situation is better compared to other sectors.
- Some organizations are doing just for the compliance.
- Threat is high, investment is low.
- Awareness is only to the limited commercial banks. Other institutions lacks motivation on investing in cyber security.
Airlines/Aviation Sector
Aviation sector heavily rely on information and communications technology systems and continue to invest in new and innovative OTs to increase speed and reliability. This increases the scale and complexity of aviation cyber security risk as reliance on cutting-edge, yet less mature, OTs might bring significant improvements but could also expose airports to new risks and unknown threats.
Why aviation industry become the prime target
The answer is quite simple, it’s for data. Airlines collect the enormous amount of data including credit card information and passport numbers, from their reservation and scheduling systems and frequent flyer programs. For attackers hoping to cash in on sensitive data, the aviation industry is a gold mine. Recent hacks on the aviation have been a wake-up call for how real is the cyber threat.
Nepal Aviation situation
- Not following any security compliance yet
- The system is poor and easily exploitable.
- Data of international and national visitors on high risk
- The exploited system can be used National and international crime use. , and can also be used for political agendas.
Hydropower Sector
Every component of society is becoming more connected to the internet, including hydropower facilities. Dams supply electricity to the United States’ grid, powering everything from homes to electrical devices.
As internet connectivity, access, and automation increases, so do the risks of compromises to hydropower operations and security. It’s vital to protect internet-connected devices, including those integrated with hydropower, from cyberattacks.
Nepal HydroPower situation
- Cyber security activity is less
- Nepal is rich in hydro source, but its system is not yet IT friendly.
- Power grid shut down is one of the threats, but impact in country like Nepal is less.
- For country reputation and with the digitization, security policy formation is needed.
Health Sector
Hacking affects every industry and sector. That reality became painfully clear in mid-May, when a cyberattacked using the WannaCry ransomware crippled health-care institutions and a variety of other organizations around the world. According to reports submitted to the U.S. Department of Health and Human Services' Office for Civil Rights, over 113 million Americans' health records were exposed in 2015, and over 16 million in 2016. Experian predicted at the start of 2017 that the health care sector would be the most heavily targeted vertical industry. According to a March 2017 report from the Identity Theft Resource Center, more than 25% of all data breaches were related to health care globally.
Three reasons health care is source of so much stolen data right now:
To begin, health-care data can be monetized. Cybercriminals, for example, can use medical data to sell fake identities, create synthetic identities, and enable someone to commit medical identity theft. If that doesn't work, they can use the stolen information for traditional identity theft, because medical information typically contains enough information for a criminal to open a credit card, bank account, or loan in the victim's name. If neither of these options works, cybercriminals can use ransomware to extort money from health care organizations in order to regain access to compromised systems and data.
Second, health-care organizations have been slow to adopt practices that have proven successful in other industries. The majority of health care portals, for example, lack strong multifactor authentication. Many medical professionals are unaware of the dangers to data security (which is ironic given the strong emphasis on patient privacy). Furthermore, health care organizations have smaller security budgets and teams than financial services organizations.
Finally, as other industries became more sophisticated in detecting and blocking cyberattacks, criminals were forced to seek out new data sources. Apart from the fact that health-care institutions collectively hold information on the vast majority of the population, their IT systems are also linked to financial services (e.g., flexible spending accounts with their own debit cards or health savings accounts that can have five-figure balances after two to three years).
Educational Sector
Educational sector is a place from where knowledge should have been driven. But the system of these sectors is itself poor.
Even when the systems are compositable and has been notified to authorities, personnel remain passive and ignorant.
Need authorities to govern cyber-security policy
Government Sector
Cyber Security in government is the most needed, but very neglected in Nepal. Due to political instability and corruption, cyber security initiations are very slow and many time initiated but not properly executed. Quality and knowledge are very poor.
Situation in Nepal
· Overall system quality is low.
· Many Systems are easily hackable.
· Lots of attacks are being surfaced and being neglected.
· Beginners and even schools’ students are using the government portal as a testing platform.
· The negligence of governmental sector is causing overall reputational damage to entire IT sector of Nepal.
Where Nepal is lacking on
International Telecommunication Union (ITU) Nepal has ranked Nepal in the 94th position in the Global Cybersecurity Index in 2020. Its security awareness is increasing, but still not good enough.
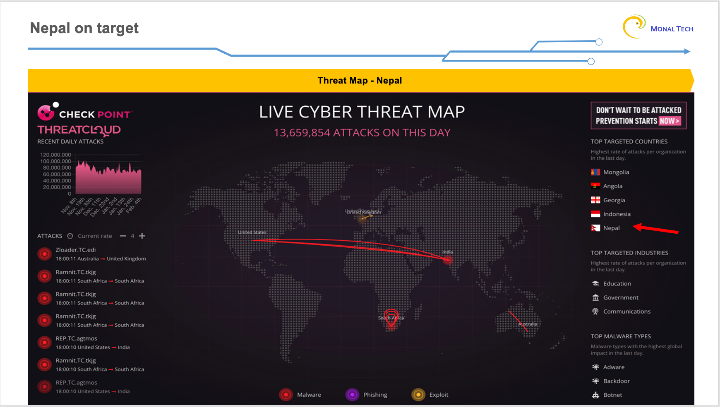
Nepal is consistently on the top targeted country in cyber security threat map.
Building a cyber security framework and team in Nepal is like building an army team. The team needs to be focused, highly experienced, have superior power.
Unlike focusing on finances, focus must be on the data. Data is equally import; however, its security is not given enough importance. Data breach penalty is also not executed. There needs to be body where data breach must be reported, and penalty must be executed.
There is lack of consistency in the cybersecurity policy in different sectors of Nepalese Organization. Most sector lacks cyber security policy.
The spending in cyber security is less and some are doing it just for the compliance and many are not focusing on it because there are no mandates as such.
Due
to lack of expertise in the domain, public are suffering from consulting help.
Recommendations
Update HIPAA
Like the PCI DSS rules for debit and credit card security, the HIPAA Security Rule and the HIPAA Privacy Rule are already well-known frameworks for defining how a health care organization should secure its people, systems, data, and equipment.
Adopt “tokenization”
This approach, which involves replacing sensitive data with other unique but no sensitive data, has been popular in the credit card industry for several years. It is an appropriate method of data protection in situations where a consumer (i.e., a patient) is involved in some type of card-based transaction. This could include using a flexible spending account or paying a health care bill online.
Experiment with blockchain
The technology can record transactions between two parties efficiently and in a verifiable and permanent way. It is being used in financial services as well as other areas. For instance, after Estonia suffered a significant cyberbreach in 2007, the country became more aggressive about protecting its society and is now using blockchain to protect its citizens’ medical data. Several blockchain-based identities-credentialing systems exist, including Guardtime, TruCred, Civic, and OneName.
Require training for personnel
Human error, including falling for phishing attacks, is the leading cause of major security breaches today. Health care systems should regularly remind people of the importance of information security best practices through required training, strategic reminders, and other means.
Deploy strong authentication
Multifactor authentication or other types of consumer security that are already common in the financial services industry in the United States should be used by health care systems. Most consumers in the United States are already familiar with this type of technology and will not need to be significantly reeducated (a challenge the financial services sector had to deal with a decade ago).
Transparency and Information Sharing
The aviation sector is a global, interdependent system with many common systems and cyber-attacks can easily spread and have global impact. The objective of transparency and information sharing is to allow for prevention, early detection and mitigation of relevant cybersecurity events before they lead to wider effects on aviation safety or security
Incident Management and Emergency Planning
There is a need, in line with existing incident management mechanisms, to have appropriate and scalable plans that provide for the continuity of air transport during cyber incidents. It is recommended that States and the aviation sector make use of existing contingency plans that are already developed and amend these to include provisions for cybersecurity
Practice of Standard Regulation
Internationally recognized cyber security framework like ISO/IEC 27001, GDPR, NIST SP 800 etc must be practiced for defining how organization should secure its people, data, systems and other infrastructure.
Take Holistic Risk Management Approach to Cyber Security: Cyber Security is not a stand-alone risk that aviation sector face. It should be included in a holistic and enterprise-wide risk management approach to ensure all aspects are addressed across the business. It will help to identify
Zero-Trust Network Model
While zero-trust has existed for quite some time by now, not all organizations have adopted it. Layering zero-trust policies into your security architecture can limit liabilities in the event of a network intrusion.
Ways Firms can improve security:
1. Obtain security systems that can provide real-time assessments of your compliance. Ensure that organization invest in a security solution that can meet the rigors of BASEL, SOX, NIST and GDPR requirements.
2. Right after compliance, firms need to focus on obtaining comprehensive threat visibility. A unified management solution and a consolidated cyber security approach can lead to greater preemptive protection against sophisticated and advanced threats. In some cases, unified security can lead to a 50% increase in operational efficiency and lower total security costs.
3. Invest in a strong endpoint security solution. Organizations have endpoints everywhere. Credit card readers and ATMs represent physical means of accessing a financial firms’ network. Sophisticated criminals can cram malware onto physical machines and/or can leverage man-in-the-middle attacks to steal money or information.
4. Implement zero trust. A zero-trust methodology can ensure that only those who need access to certain systems can obtain it. In the case of credential theft, a zero-trust approach reduces the likelihood that a hacker will access sensitive computing data.
5. Ensure that third-party partners do not present security risks. Firms can request for third-party groups to undergo risk assessments and periodic risk audits.
6. Provide employees with cyber security awareness training. Over 80% of data breaches involve a phishing attack. Employees need to know how to recognize these types of threats and others. Consider ongoing training campaigns and approachable means of conveying critical cybercrime concepts.
7. Robust mobile security. The anywhere anytime approach to banking offers customers extensive convenience, but only when mobile phone threats are not a menace. Cyber criminals are quick to deploy malware that can manipulate mobile baking apps. In this day in age, Firms would be sorely remiss in lacking comprehensive mobile-first threat prevention strategies.
8. Developing quality customer services is a crucial step in safeguarding organization brand, institution, and network. If a customer experiencing a security issue cannot quickly and easily get ahold of an institutional representative, a cyber security problem may escalate and/or expand. This could affect your firm on a larger level.
9. A holistic approach to cyber security is needed. It is incumbent upon IT departments to connect with other departments across the firm to develop a business-wide cyber security strategy. This can help cyber security professionals spot weaknesses, close security gaps, and avoid future threats.
10. Improve organization response time in the event of a breach; ensure that organization has an incident response plan in-place. With ample advanced planning, schedule a cyber security drill and test out incident response blueprints. Organization may want to schedule several drills to test out plan at different hours of the day or with different staff members on-hand.
Conclusion
There is no doubt that cyber security is one of the major global concerns. Nepal, situated between big pillars like China and India, cannot hide from cyber security issues. When a country is launching big digitization projects and being IT-friendly, cyber security framework establishment is the most important part.
Many rumors are going on internationally about Nepal. All are not true, but then sufficient research, expertizing and investment are needed in this sector.
The Cyber Security field needs to be a politically free sector and its project needs to be fast-tracked.